Robert Frost
American Poet in Mending Walls (1914)
Good fences make good neighbors.

February xx, 2025
Most boards consider cybersecurity a necessary expense, like insurance, to remain a going concern. However, this report reveals how cybersecurity can be a strategic investment that generates business value and a competitive edge. Our focus is on the potential of a cyber secure organisation to create a strategic advantage. We don't dwell on the need to protect, but rather we should consider how to exploit a security advantage in a networked society.
The economy comprises many digitally connected enterprises (e.g., Amazon and its buyers and sellers). Most organisational associations are mediated or influenced by digital ecosystems (e.g., e-commerce platforms). The many digital linkages mean there are manifold dependencies among organisations. Businesses rely on a network of suppliers and customers to remain ongoing concerns.
Digital dependencies create transitivity threats. Mathematically, transitivity is when A → B and B → C, then A → C. In a chain of relationships, it implies that when A fails, B and C also fail. Transitivity chains can be long in a digital global society, and threats are often unrecognised until a link fails. The viability of an economy is threatened when chains of dependencies are not secure. In particular, when the tail of a network fails, there can be a domino effect, as we saw with Optus, which threw Australian national payment, transport, emergency services, and health systems into chaos, and Crowdstrike when 57% of US scheduled airline routes had significant delays. Supply chain risks, such as the prior examples, can strike many organisations.
Minimising or eliminating transitivity effects requires securing and replicating dependencies across connected organisations’ core assets, such as energy, communication, and raw materials, to prevent rapidly rippling waves of failures. In a digital world, it means hardening critical components, such as the Internet infrastructure. Where possible, dependencies should be dynamically replicable. For instance, in the case of the Optus outage, critical linkages should have been immediately connected to other telecommunication providers. At the same time, recovery actions must be 'recovery-safe' to avoid the originating supplier's failure infecting its replacements.
Cybersecurity limits transitivity tsunamis by protecting direct consumers of an organisation's connected capital and system. An investment by those at the beginning of a network chain (e.g., electricity generation) can have immense benefits for those further along the chain. Cybersecurity, like a standing defence force, is a societal investment. It depends on many organisations investing wisely in collective safeguarding. Those who invest well can raise their capital productivity by attracting suppliers and consumers who value security, dependability, and business continuity.
We can learn from Toyota's Total Quality Management philosophy. It invests in raising the quality of its physical supply chain to ensure that suppliers' components meet its standards. The Victorian Department of Transport emulated this approach by pushing security down to Yarra Trams, which pushed it further down to its suppliers and so on down the chain. Powerful customers can raise the cybersecurity standards of their suppliers.
Robert Frost American Poet in Mending Walls (1914) Good fences make good neighbors. |
|
As we have discussed before, an organisation is a capital creation system, typically embedded in a digital network. The following figure shows its key stakeholders are its suppliers and customers. Organisations depend on suppliers for essential capital and systems. In return, suppliers want reliable customers whose business continuity is assured, and they might be willing to give them preferential treatment.
Conversely, customers want suppliers who can be relied upon to deliver capital and systems, and they may be willing to pay a premium price to avoid disruptions to their business.
Cybersecurity must be viewed holistically and strategically as a partnership between immediate suppliers and customers. It is a neighbourly investment that ensures joint operational continuity.
A competitive economy is a vast network of digitally connected suppliers and customers. It is a series of mutually dependent relationships whose reliability determines organisational and national success. The partitioning of cybersecurity across the digital economy is a critical government decision. For example, should spam policing be the task of the national government, Internet providers, or individuals? What are the continuity responsibilities of the suppliers of critical societal services, such as emergency phone calls?
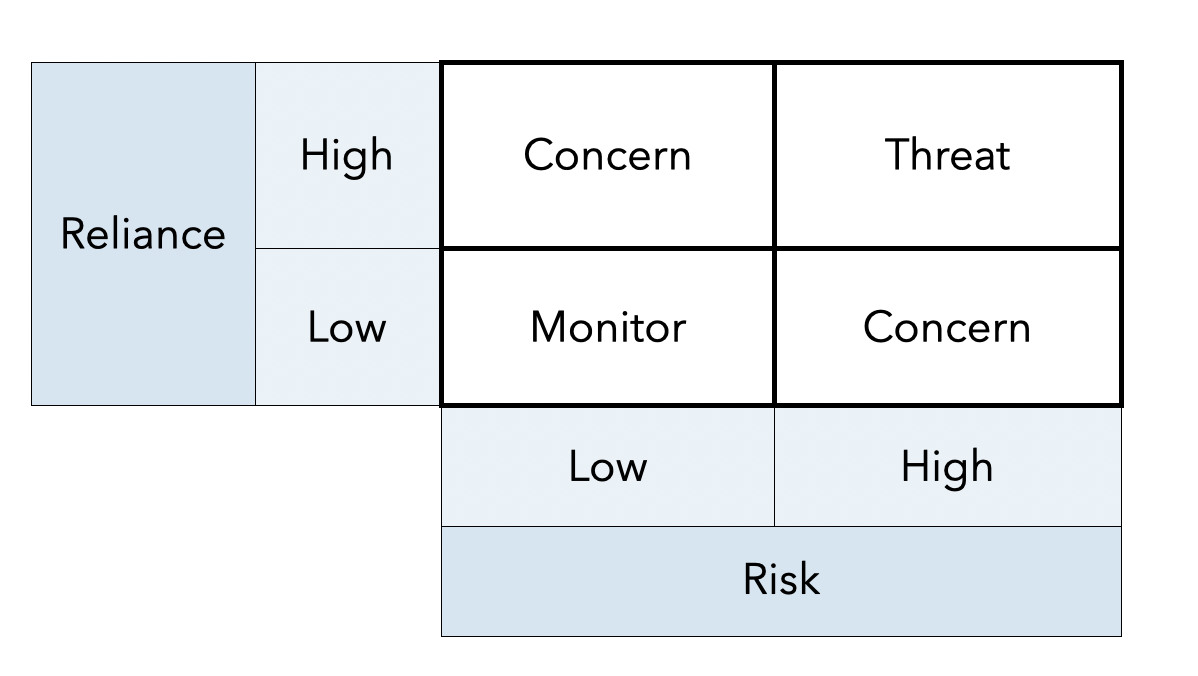
All suppliers should be evaluated regarding your reliance on their capital or systems, as shown in the following figure. For high-risk suppliers, you should take immediate action. Duplicating suppliers is a common solution. It depends, however, on an alternative supplier(s) having sufficient excess capacity to meet your critical needs when the lead supplier fails. Australia relies on duopolies for food and air transport. If one fails, could the other step in? Could Woolies take over from Coles, or Virgin from Qantas?
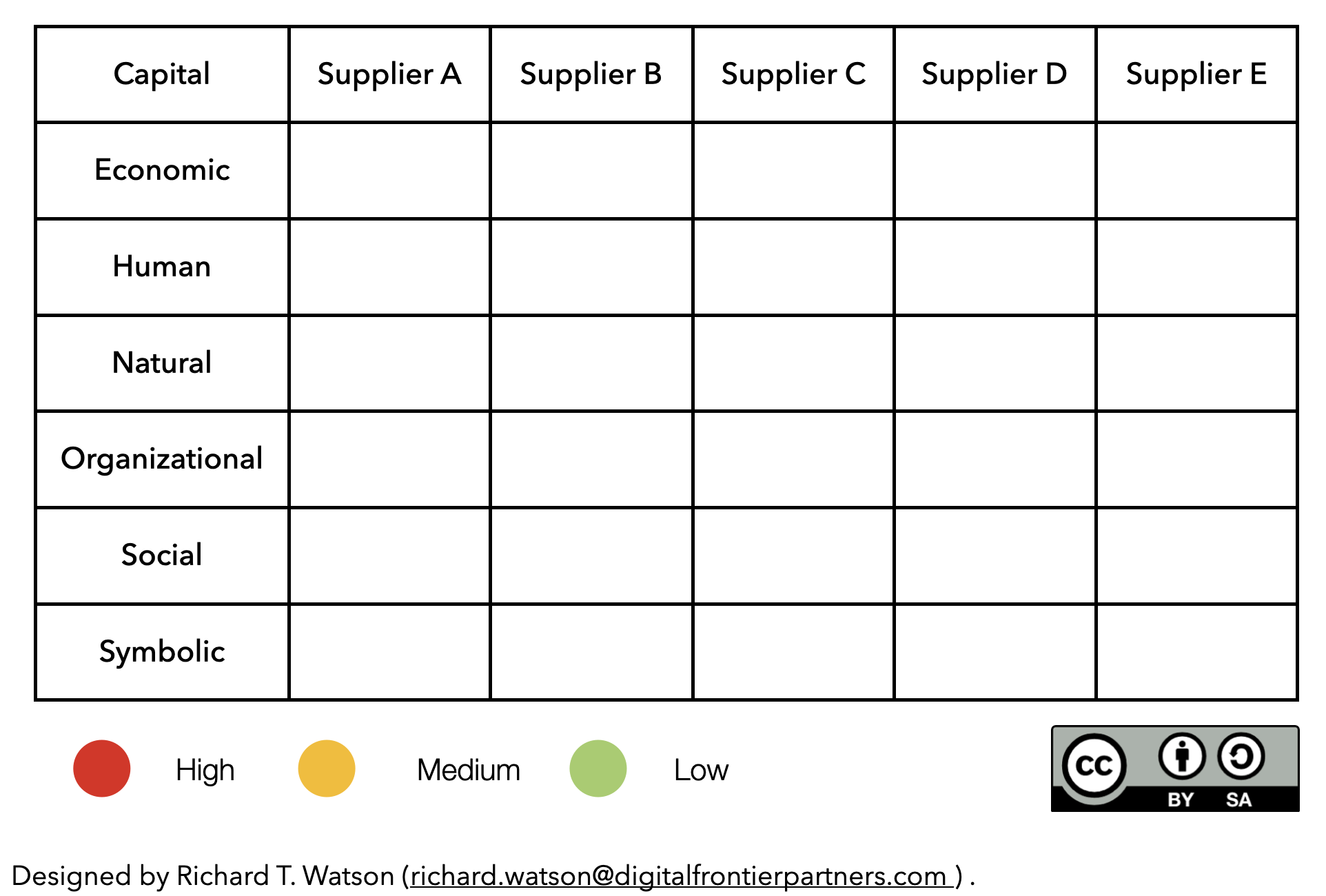
You could request an independent third party to assess all threat-level suppliers' cybersecurity. This due diligence analysis could look at your cyber status from both directions. Can you assure a valued supplier that a cyber failure on your side is low risk? In a connected world, cyber attacks can flow in both directions.
Of course, a supplier might fail for other reasons, such as financial or product quality issues. A comprehensive supplier risk analysis should assess all risks regularly.
If you have sufficient power, such as Toyota, you can require your suppliers to use the same risk analysis to assess their suppliers. You want 'good fences' in all stages of a supply chain.
If your customers include businesses and the government, you should ask them to use the preceding figure to assess their perception of the risk of doing business with you. You should primarily address the high-risk column, even when their reliance on you is low. Your concern for providing a secure service sends a message about your business and might influence future procurement decisions.
Customer retention is the primary benefit of cyber investments for consumer-facing organisations. However, customer recruitment is typically more expensive than customer retention. Furthermore, when you lose a customer, you also lose what you have learnt about marketing to them. With a new customer, you have to restart the learning process.
Jeh Johnson US Secretary of Homeland Security (2013-2017) Cybersecurity is a shared responsibility, and it boils down to this, in cybersecurity, the more systems we secure, the more secure we all are. |
|
Security can apply to many contexts, as the prior quote implies. In this report, the theme is protecting an organisation's capital. In an earlier post, we introduced the notion that all organisations are in the business of generating capital. By protecting its capital, a business shields its suppliers' and customers' capital-generating capacity (e.g., revenue stream). In a digital world, you have many neighbours, and your neighbours have many neighbours. We now examine each type of capital and its particular cyber investment opportunity.
Implicit in the capital-oriented perspective is the notion that cybersecurity is a property or attribute of each type of capital. This framing facilitates a finer-grained analysis of cybersecurity to embrace the mix of capital an organisation needs to deploy to remain a competitive entity.
Economic capital covers financial, physical, and manufactured resources. It is now common for physical resources to be integrated into the Internet of Things (IoT) and thus open to cyber attacks. Production equipment can be particularly exposed because it is not usually integrated into the information technology infrastructure. As a result, equipment operating systems might be outdated. Because an attack on equipment will disrupt production and impact customers, investing in securing physical resources raises business continuity for suppliers and customers.
A workforce's skills, knowledge, and abilities are essential for efficient and effective operations. An organisation's computer systems might be secure, but people can be exposed to cyber risks via personal computers. A major danger is when a malicious party threatens to reveal embarrassing behaviour unless a fee is paid. Such extortion is an organisational threat, especially if the cost is high, because the targeted person might divert corporate resources to pay the blackmailer. Additionally, an employee under threat will likely be distracted and less productive. Investing in a psychologically safe process to enable cyber-threatened employees to report such attacks and get organisational support to resolve the issue should be part of a cybersecurity policy..
Natural capital refers to the rights to use or extract natural resources, such as farming and mining, both information-intensive activities today. In April 2023, an Inmarsat-41 satellite outage rendered innovative farming equipment reliant on GPS inoperative in Australia and New Zealand. Farmers had to resort to less accurate free-to-air GPS or manual processes. Precision farming and mining depend on Internet and GPS access, and productivity drops when either connection is severed.
Organisational capital is becoming increasingly important because it comprises digitised knowledge (databases), standardised procedures (software), routines, patents, and operational guidelines. A short-term loss of some of these critical resources can interrupt inbound (e.g., customers' orders) and outbound digital (supply coordination) traffic. A long-term loss jeopardises business continuity for one or more portions of a supply web.
Social capital is an organisation's web of community relationships. The value of these social connections diminishes when critical stakeholder communications are disrupted. Typically, third parties supply the necessary infrastructure for such communications, and their cybersecurity issues can impact your social capital.
Symbolic capital is an organisation's reputation. It is its public image, the value of its brands, and its prestige. Symbolic capital is created when your performance significantly exceeds expectations. Symbolic capital, like reputation, can take years to build and days to evaporate. Performance shortcomings caused by cybersecurity shortfalls will likely damage symbolic capital and impact your ability to command a premium price and retain customers.
The tail of a digital supply chain is frequently the most critical connection. A failure of a vital tail resource, such as electricity, will affect many, including your suppliers, you, and your customers. Investments in tail duplication and redundancy protect your capital. Invest strategically using the following grid to assess the risk of rippling tail failures and the opportunities afforded by assuring your customers you have a comprehensive approach to securing the critical capital they rely upon.
Sarit KannanoorConsulting CISO Comments and conversations are welcome. |
|
Rick WatsonResearch Director Comments and conversations are welcome. |
|